
The administration and protection of knowledge, information, and data is known as information assurance and security. It combines two fields: information assurance, which focuses on ensuring the availability, integrity, authentication, confidentiality, and non-repudiation of information and systems, and information security, which focuses on ensuring the availability, integrity, authentication, confidentiality, and non-repudiation of information and systems.
Components Information Security Assurance?
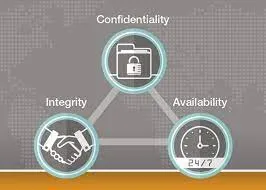
- AVAILABILITY
Availability refers to how users are given access to sensitive information within your enterprise’s infrastructure.
Privileged information should not be readily available, as that can make it all too easy for hackers to obtain. But if the data is too difficult to access, then employees might not be able to perform critical job functions in a timely manner, costing your company lost time and revenue.
Availability also takes into consideration if and how sensitive information will be accessed, even if the information systems fail partially or fully. For instance, if a database failover occurs, ideally employees would still be able to access the information most critical to their business operations.
To ensure the continued availability of sensitive information only to a select few, security professionals will generally put measures such as firewalls and load balancers into place.
- INTEGRITY
Integrity, as a principle of information assurance, means that your sensitive data is not tampered with in any way.
Antivirus software, penetration tests, and other security measures are often employed to ensure that your data’s integrity is not compromised by hackers. If malicious code or malware did manage to infect the data, your sensitive information could potentially be altered or deleted. Ideally, your company would use proactive cybersecurity measures to keep intruders from ever accessing your data in the first place.
Integrity also relates to user controls designed to prevent any meddling with sensitive data. Privileged users need to understand how to properly send information from one location to another without accidentally altering the data—or situating the data in such a way that it is easier for hackers to access.
Some organizations use hash signatures when transmitting sensitive data from one location to another. This allows them to confirm that the data has not been compromised while in transit.
- CONFIDENTIALITY- Perhaps the most important principle of information assurance is confidentiality. Only users who need to access sensitive information should ever be able to view, store, alter (in approved ways), or transmit this data. Confidentiality is preserved not only through access controls, but also data encryption methods. When data encryption is utilized, users without access to the information will just see nonsensical text. Only users with an encryption key, or a password of some kind, will be able to view the information as written.
Differentiate the Governance and Risk management?

The whole set of rules, policies, and standards that guide a firm is known as governance, or corporate governance. Risk management, often known as enterprise risk management, is the process of recognizing potential company risks and taking steps to mitigate or eliminate their financial impact.
Different between Security Architecture to Design?

A security system's security architecture is the set of resources and components that enable it to function. The approaches and procedures that place those hardware and software parts to promote security are referred to as security design. Handshakes and authentication are examples of network security design elements.
Different between Business Continuity Planning to D-i-s-a-s-t-e-r Recovery Planning?
Disaster recovery focuses on recovering data access and IT infrastructure after a disaster, whereas business continuity focuses on keeping businesses running during a disaster. Meanwhile, a disaster recovery strategy ensures that an organization may resume normal operations following a crisis.
What is Physical Security Control?

