Good day, everyone!
Atharv here from India. In hive.io, I discovered a security flaw. As a result, I decided to create a blog post about it.
A vulnerability I'll discuss isn't new; it's a well-known pattern among web developers. However, not many people considered it from a security standpoint, and I had never seen it discussed in any security paper, so I decided to bring it up.
What is an Open Redirect?
As a result, we should already be familiar with the term "open redirect." If you don't know, it's when an unauthorized person can set any value as a redirect destination. Consider the following “legitimate” redirect chain:
https://example.com/login?redirectUrl=https://app.example.com
Which leads to app.example.com in the end.But what if someone malforms this url into following:
https://example.com/login?redirectUrl=https://evil.com
You'll notice that the end destination has changed from app.example.com to evil.com. It's an open redirect vulnerability if the web app allows that URL change and we're eventually redirected to https://evil.com. This behaviour could be used with other vulnerabilities like SSRF to perform phishing attacks or steal access tokens from authentication flows. There are numerous things that can be done
Vulnerable URL : https://developers.hive.io//evil.com/..;/css
I reported this bug immediately to hive security. After a few days, The hive security team was able to resolve the issue.
Some dorks to finding Open redirection Vulnerability:
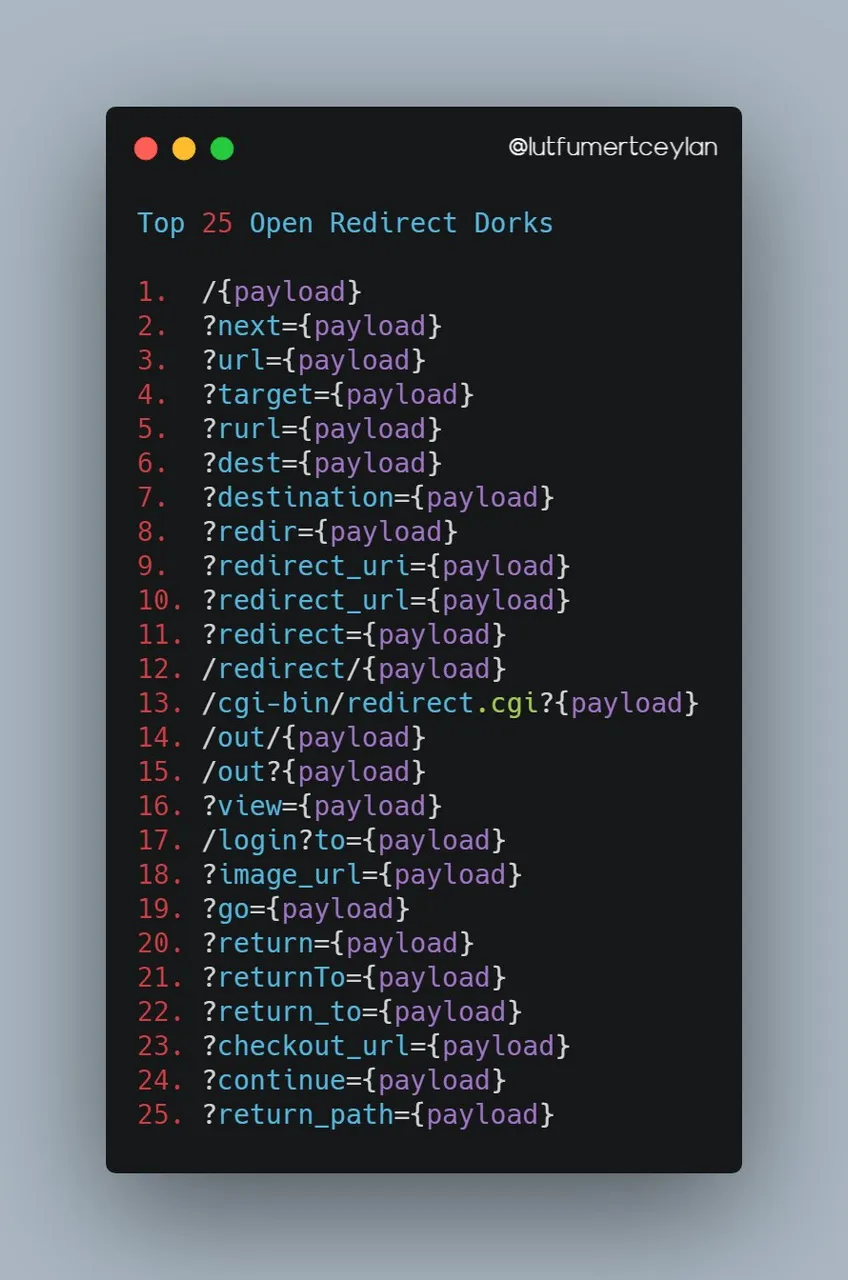
Please upvote if you learn something :)
Thanks.
