INFORMATION ASSURANCE AND SECURITY
What is Information Assurance and Security?
Information Assurance and Security is the management and protection of knowledge, information and data. It combines two fields: Information Assurance and Information Security.
Information Assurance
Focuses on ensuring the availability, integrity, authentication, confidentiality and non-repudiation og informations and systems.

Information Security
Centers on the protection of information and information systems for unauthorized access, use, disclosure, disruption, modification, or destruction - in order to provide confidentiality, integrity and availability.

What are the components of Information Assurance and Security?
Information Assurance and Security has a five (5) components or pillars, these pillars make up a specific information assurance strategy that ensures the highest level of success for organization that applies it to their daily operations.

These pillars represents the components of Information Assurance and Security which are:
- Availability. Only the users can access the data stored in their networks.
- Integrity.To set up safeguards that determined threats.
- Authentication. Verify a user's identity before allowing them to access data.
- Confidentiality. Protecting private information from disclosure to any unauthorized users systems.
- Non-repudiation. To confirm the individual responsible for processing certain data.
It is important to implement these five (5) pillars of information assurance and security because they monitor the networks to keep tracks of any possible security breaches, and they investigate any that they find.
Governance and Risk Management
Governance. The overall system of rules, practices, and standards that guide a business.

Risk Management. The process of identifying potential hazards to the business and acting to reduce or eliminate their financial impact.

Security Architecture and Security Design
Security Architecture. A set of security principles, methods and models designed to align to your objectives and help keep your organization safe from cyber threats.
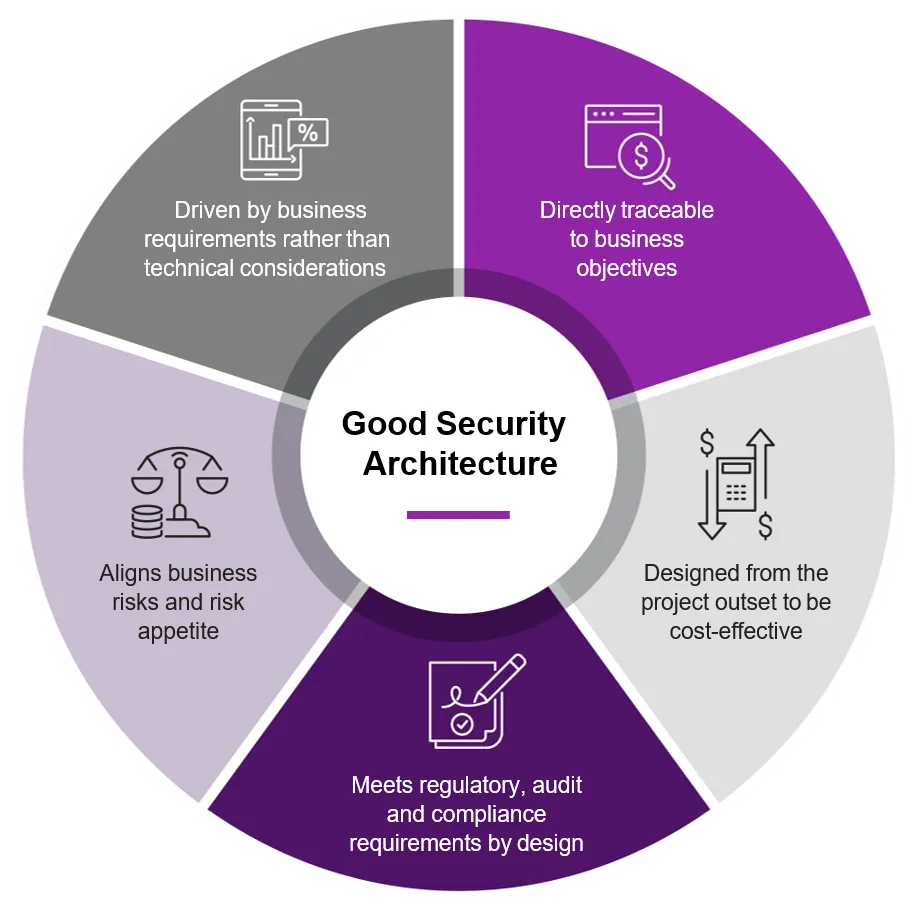
Security Design. Refers to the techniques and methods that position those hardware and software elements to facilitate security.
Business Continuity and Disaster Recovery
The Business Continuity and Disaster Recovery is a set of processes and techniques used to help an organization to recover from a disaster and continue the routine business operation.
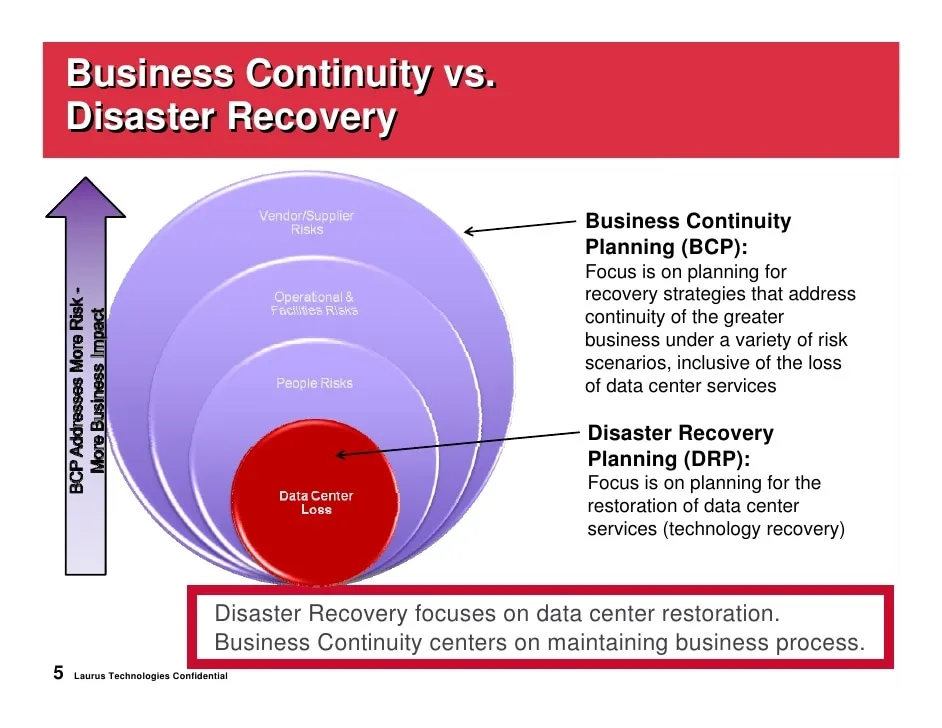
What are their differences?
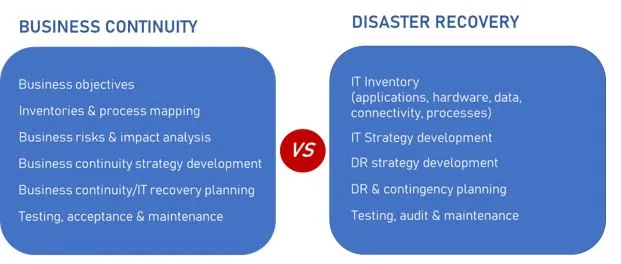
Therefore, the key differences is when the plan takes effect.
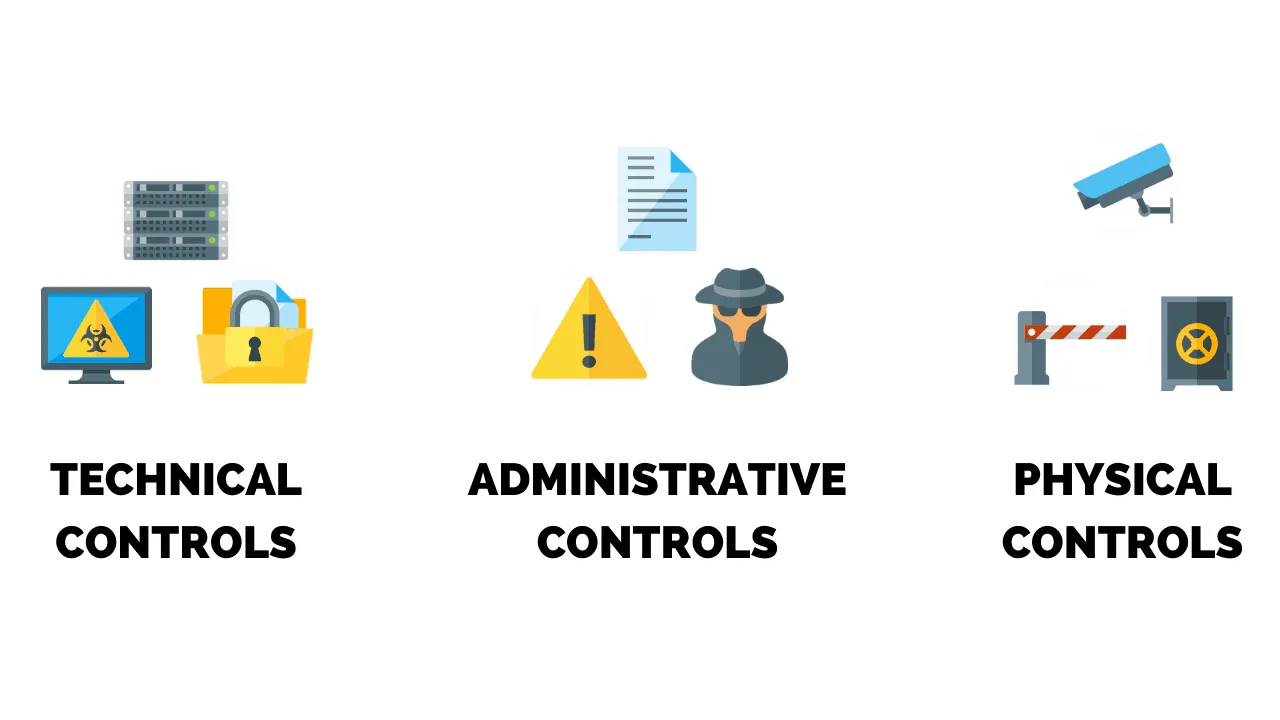
What is Physical Security Control?
Physical Security Control is the implementation of security measures in a defined structure used to prevent unauthorized access to sensitive materials. (E.g. Surveillance camera, motion or thermal alarms, security guards.)
What is Operations Security?
Operations Security is a systematic process for is meant to access the importance of information assets and to determine the best way to protect it.

What is Law?

We all know that law is a rule made by government that states hoe people may and may not behave in society and in business.
What is Investigation?

What is Ethics?
Ethics is the rational reflection on what is right, what is wrong, what is just, what is unjust, what is good, what is bad in terms of human behavior.

I hope you've learned something. Thank you for your time reading this.
